
 |
Windows 10 FAQ |
If you have recently bought or set up a PC then I suggest you take the following steps to secure your PC:
1. Enable or Install a Firewall
A firewall will block unwanted incoming and outgoing attacks to or from your PC. It will prevent trojans and worms attacking your PC such as the MSBlast (or W32/Lovsan). Windows 10 has the Windows Firewall installed, which blocks incoming and some outgoing connections , use that wherever possible if you don`t have a third party firewall (see the Advanced tab of your Internet connection). Some ADSL Modems will have a firewall, check documentation on your modem to see if it has one and whether its enabled.
To enable the firewall, open Settings, Network & Internet, Windows Firewall.
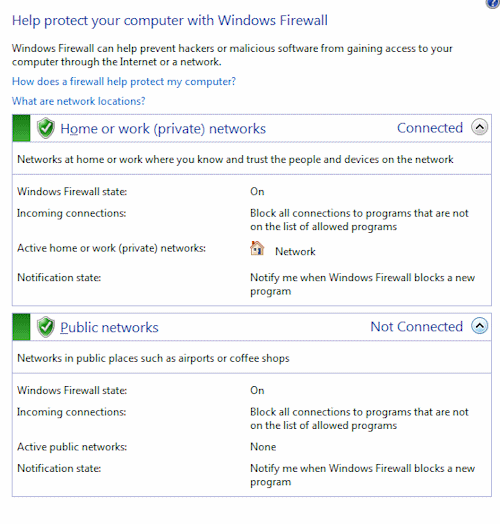
You can also buy or download a wide range of Firewall products such as McAfee, Norton 360, Sophos, ZoneAlarm, Panda Firewall, AVG , Avast, Kaspersky, Microsoft Defender and so on.
a) How to I allow Pings to my computers through a Firewall?
In the Advanced Settings, Inbound Rules, allow access for File and Print Sharing (Echo Request - ICMP v4-In).
b) How to do I allow other users access to my website through the Firewall?
In the Advanced Settings, Inbound Rules, allow access for World Wide Web Services (HTTP traffic-In).
c) How do I allow other users access to my shared folders and printers through the Firewall?
In the Advanced Settings, Inbound Rules, allow access for File and Print Sharing (LLMNR, NN Datagram, NB-Name, NB-Session, SMB and Spooler Service).
2. Install an Anti-Virus Product.
Firewalls will protect against some forms of attack but not all. Viruses come
in all sorts of forms such as Macros, Programs, scripts and so on. Only an antivirus
program will block and delete such threats. Windows Defender on Windows 10 can now detect and remore viruses and malware for you . Alternatively, there are many other anti-virus products
to list see, Product List.
For more information on viruses, see the Threat Center for latest outbreaks, symptoms and removal instructions.
3. Use your Attachment blocking in your Mail Program.
Some Email programs such as Outlook and Windows Mail will block downloading and execution of certain types of programs. For example, you can block viruses in Windows Mail by enabling blocking via Safety Options, Security and enable Do not allow attachments to be saved or opened that could potentially be a virus. You may disable this if you need access to attachment when needed, but leave it enabled at all other times!
4. Install an Anti-Spyware product
A lot of websites use suitable tricks to track and download private information
about your self and your web browsing habits and tend to install plugins and
programs that sometime hijack your browser to set your home page or display
pop ups. Programs such as Defender
can search and remove such products from your system. Ideally use two or more
anti-spyware products as one may not detect them all. If you have User Account
Control enabled, it will prevent malware from installing programs without your
permission.
You can also restrict the types of cookies saved to your PC via the options
in your Web Browser. For example, in Internet Explorer, use Tools, Internet
Options, Privacy and set a privacy level to suit your web sites (Medium
is suitable in most cases).
Use either Task Manager, MSCONFIG or the FarBar tool and check safe programs
listed under startup and make sure they are required, to check whether
a program is causing problems.
5. Clear out your Temporary Internet Files cache and Cookies cache
Copies of web pages and pictures are saved in a cache on your PC, clearing this cache out on a regular basis (no more than once a week) will remove any unwanted files. In Internet Explorer, goto Tools, Options, Delete Files or Delete Cookies. Using the Disk Cleanup facility can also clear out the cache. In Edge, go to Settings, Privacy, Search and Services and select 'Clear browsing data now'.
6. Use more secure file systems
Where possible use more secure file systems such as NTFS on Windows NT,2000,XP, Vista,7,8 rather than FAT32 to secure your files and if possible. If you have Windows 10 Pro then you can take advantage of EFS (Encrypted File System) to secure data on the hard disk (make sure you back up data and certificates before using EFS). If you loose your certificate or account then it will be impossible to recover the data.
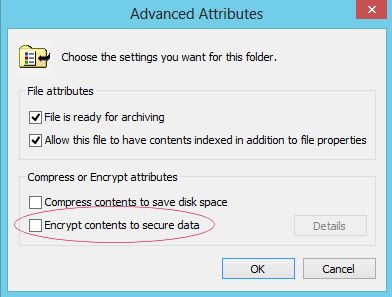
Make sure you backup your personal certificate to a Floppy or USB stick, because if you loose that and need to recover data, it will be impossible to read the data again. See the Certificates management console.
7. Keep your PC up to date with latest security patches
Wherever possible keep your PC updated with latest security updates by enabling 'Get latest updates as soon as they're available' option in Settings, Windows updates.
Alternative methods of updates can be download direct from Microsoft Update Catalog or download updates from a fast internet connection using WSusOffline, and then transfer and install the updates on to PC that have no or slow internet access.
8. Backup your data
Get a decent backup program in case your PC is infected, attacked or otherwise
made unusable and require a reinstall. Programs are easily to reinstall but
data is very hard to get back if deleted, overwritten or lost.
Windows 10 includes File History which can backup a 'history' of files to an external drive. You also use OneDrive for 'cloud' based storage.
9. Secure PC with usernames and passwords
Use a Standard user than an Administrator user when using your PC. . Linux or other unix systems tend to be secure but double check your setup anyway for any loop holes. Also, make sure that you always set a password for accounts including the administrator account, which is blank by default on most Destkop systems. Never write passwords down where they can be easily found and use complex passwords, using combinations of letters and digits and do not use personal information for passwords e.g. names, date of births, pets etc. which can be easily broken.
Never give out personal information such as account details, pins numbers or passwords from Emails sent over the network. Legitimate companies and banks will never ask for such information even if threatened with Account closure or suspension and never click on links provided on such Emails as they will always be sent to fake web sites.
Windows 10 supports biometric security such as Face recognition or Fingerprints using Windows Hello, a PIN number instead of a pasword or a Picture Password. See Settings, Accounts, Sign-in Options.
10. Clear out your Contacts
A lot of viruses now uses your contacts to spread itself to other users. I suggest you delete any unwanted or old email contacts from your Address Book now and again. Also, so keep your Address book clear, turn off 'Automatically put people I reply to in my Contacts list' in the Send options of Windows Mail or any other email program, so that it doesn`t fill up with unused entries and restricts the number of potential victims of viruses! You can still add people by right clicking their email address in a message and selecting 'Add to contacts'.
11. Do not use Peer-to-Peer File Sharing Software.
File sharing software basically allows anyone to read files off your computer and bypasses your Firewall and all other security considerations. Consider this as a very risky. If so, do NOT login with an account which has administrator privileges, and apply strict NTFS permissions to the folder you use for file sharing and keep it well away from any personal data.
12. Do not advertise your email address.
Your email address can be searched for and use for spam very easily by programs that actively look for email addresses than can be used to spread spam. If you have your own web site DO NOT use the standard technique of using HREF and the MAILTO: method of displaying your email address, instead use Javascript to hide it from spammers and search programs (called webbots). If you visit a website and need to create a profile or login name, if it asks for an email address either enable the option to hide the address from public view or use another email address instead of your main email address.
13. Erase your hard disk before selling or recycling your old PC.
Programs and data can be easily stolen from hard drives on old PCs.A format will not clear it, you need to overwrite the data several times with a good secure erasure program which will write loads of 00000s then 11111s and 1010101s Good programs include software such as Drive Wipe. For more permanent destruction you could use a powerful magnet, a drill or a hammer to destroy the disk (only for the most paranoid users).
14. Make sure data is secure by using EFS or third party products
If you listen to the news, computers can be stolen and you may end up losing valuable data to theives. To protect your data you should use the Encrypted File System on Windows 10 Pro or Enterprise Editions. If you have Home editions you can use other products such as Folder Guard, DES Lock+, and Symantec Endpoint Encryption products.
15. Enable security options in your Browser
In Internet Explorer you should enable UAC (User Account Control) which will
enable Protected
Mode (see status bar at the bottom right), also enable the Pop Up Blocker
to stop unwanted pops ups (although this may also disable legitimate pop up
windows), and lastly you can try InPrivate Browsing, Tracking protection and ActiveX Filtering. Switching to the Edge browser or other browser would be more secure than using IE.
To prevent phishing and downloading malware, try McAfee's
Web Advisor tool to advise you on a site's safety. For a secure browser try AVG's Secure Browser.
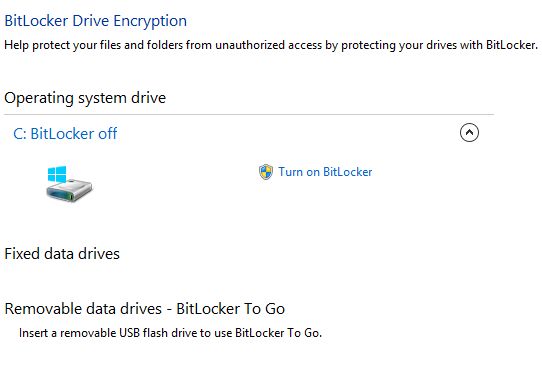
16. Use BitLocker to secure your PC
If you have Pro or Enterprise edition you can enable Bit Locker to secure your PC. To enable it, goto Control Panel, System and Security, Bitlocker. To enable Bitlocker you need to have the Trusted Platform Module (TPM) aka PTT enabled in your BIOS settings.. Also you need a single partition (C:) to take full advantage of bit locker. As you can see my PC can be BitLocked:
17. How can I secure my Wireless Network?
Wireless networks, if unsecured can be open for anyone to use and if you have an unsecure Workgroup, people can view files on your shared folders.
Windows 7 and 8 support Home Groups which can be secured with a password to restrict who can view shared files, this will only work if all the other computers are Windows 7 or 8 machines.
To secure your wireless network, you should enable encryption of all network traffic using WPA2. You should also hide the name or SSID of your wireless network to prevent people trying to connect to it. Also, you can restrict the network to specific computers and mobile devices by putting them in a Wireless Station Access List so that unknown devices cannot connect. It is also a good idea to change the router's default admin password to prevent others from changing its settings and locking you out.
18. What is SmartScreen?
SmartScreen in Windows 10 allows you to be warned about any potential threats from unrecognised apps or programs before running them. You can turn in on via the Control Center, Action Center. It is three settings:
a) Get administrator approval before running an unrecognised app.
b) Warn before running an unrecognised app but does not require administrator approval.
c) Don't do anything (turn off Smartscreen)
19. How do I re-enable Windows Defender if I remove a third party antivirus product?
Open services.msc console and make sure Windows Defender Service has been enabled and started. Then in the Search box enter Windows Defender to load the Windows Defender settings and make sure it is enabled or turned on.
20. Update your applications?
As well as keeping your Windows secure, you should make sure that your applications are secure and make sure that applications, plug-ins and other options are kept up to date. Configure the applications as securely as you can but following best practice and guides.
21. How do I securely connect to my workplace network?
The most secure way is through a Virtual Private Network, which is a secure network connection over your normal internet connection to the VPN server at your workplace. Your company will provide the right software to connect their network. To make it more secure, it should use Multi-Factor Authentication using a mobile app to add an extra level of secure authentication.
Companies should avoid direct RDP or SSH access and should use secure Jump Boxes like Azure Basition or secure remote access solutions like Parallels Remote App Server or Citrix Secure Workspace Access.
22. How does the Trusted Platform Module (TPM) work?
The Trusted Platform Module (TPM) is a special chip on the motherboard. It supplies a cryptograhic key to the system and allows the drive encryption (see Bitlocker) to be unlocked and the computer starts up. But if there is a problem with the key, such as a hacker stealing your laptop and tampers with the the encrypted drive, the PC will fail to boot up. You can check if TPM is installed or enabled by loading the TPM.msc console to view details of the chip and version. If it is not enabled, you may have to enable Platform Trust Technology (PTT) in the BIOS Chipset settings before booting into Windows. No additional changes are required in Windows for it to work.
23. How do I secure my boot files?
For Windows to load from disk, it uses various boot files which is managed by BCDEDit (Boot Configuration Data editor), these file replace the old Boot.ini on previous versions of Windows. Run BCDEDIT /enum /v to view the boot configuration.
Notice that the system loads C:\Windows\system32\winload.efi to start the system. A feature called SecureBoot allows you to protect your boot files and OS by enabling TPM chip in the BIOS settings and Secure Boot in the UEFI Firmware settings.
You can use the PowerShell, to view SecureBoot variables using Get-SecureBootUEFI and Set-SecureBootUEFI commands.