
 |
If you have recently bought or set up a PC then I suggest you take the following steps to secure your PC:
1. Install a Firewall
A firewall will block unwanted incoming and outgoing attacks to or from your PC. It will prevent trojans and worms attacking your PC such as the MSBlast (or W32/Lovsan). For example, Linux mint has the ufw, a netfilter firewall installed, which can block some incoming and some outgoing connections. It is configured from the command line or from a graphical front end such as gufw (which will need to be installed seperately). Just change the Status to on to enable the firewall.
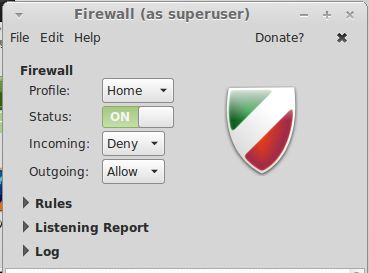
a) How to I allow Pings to my computers through a Firewall?
UFW allows ping requests (ICMP) by default, although you can control this editing the /etc/ufw/before.rules configuration files.
b) How to do I allow other users access to my website through the Firewall?
In the Rules, allow access by selecting Network for Category, Services for subcategory and then either HTTP or HTTPS.
c) How do I allow other users access to my shared folders and printers through the Firewall?
Files: In the Rules, allow access by selecting Network for Category, Services for subcategory and then select SAMBA.
Printer:
In the Rules, allow access by selecting Network for Category, Printing for subcategory and then either CUPS, HPLIP or IPP.
2. Install an Anti-Virus Products
Firewalls will protect against some forms of attack but not all. Viruses come
in all sorts of forms such as Macros, Programs, scripts and so on. Only an antivirs
program will block and delete such threats. Linux does not normally need an Antiv-virus product but one of the common ones is Clamav and commerical software such as Microsoft Defender for Linux, BitDefender Endpoint Security Tools, McAfee Endpoint Security, Sophos and Kaspersky Antivirus.
For more information on viruses, see Virus Info website on symptons and removal instructions.
5. Clear out your Temporary Internet Files cache and Cookies cache
Copies of web pages and pictures are saved in a cache on your PC, clearing this cache out on a regular basis (no more than once a week) will remove any unwanted files. In Firefox goto History, Clear Recent history which can be used to clear the cache,web page history, cookies, form information, and active login details.
6. Use more secure file systems
You can use encryption to secure sensitive documents using tools such as LUKS and Seahorse. Note. If you loose your certificate or account then it will be impossible to recover the data.
Make sure you backup your personal certificate to a external HD or USB stick, because if you loose that and need to recover data, it will be impossible to read the data again. See the Passwords and Keys tool to export your important key.
7. Keep your PC up to date with latest security patches
Wherever possible keep your PC updated with latest security updates by updating programs and libraries using Update Manager.
8. Backup your data
Get a decent backup program in case your PC is infected, attacked or otherwise made unusable and require a reinstall. Programs are easily to reinstall but data is very hard to get back if deleted, overwritten or lost. A list of backup software can be found in Software Manager. A full system image can be done using CloneZilla.
9. Secure PC with usernames and passwords
Use a Desktop user than an Administrator user when using your PC. . Linux or other unix systems tend to be secure but double check your setup anyway for any loop holes. Also, make sure that you always set a password for accounts including the administrator account,. Never write passwords down where they can be easily found and use complex passwords, using combinations of letters and digits and do not use personal information for passwords e.g. names, date of births, pets etc. which can be easily broken.
Never give out personal information such as account details, pins numbers or passwords from Emails sent over the network. Legitimate companies and banks will never ask for such information even if threatened with Account closure or suspension and never click on links provided on such Emails as they will always be sent to fake web sites.
10. Clear out your Contacts
A lot of viruses now uses your contacts to spread itself to other users. I suggest you delete any unwanted or old email contacts from your Address Book now and again. Also, so keep your Address book clear, turn off 'Automatically add outgoing email address to my Collected Addresses' of Thunderbird or any other email program, so that it doesn`t fill up with unused entries and restricts the number of potential victims of viruses! You can still add people by right clicking their email address in a message and selecting 'Add to address book'.
11. Do not use Peer-to-Peer File Sharing Software.
File sharing software basically allows anyone to read files off your computer and bypasses your Firewall and all other security considerations. Consider this as a very risky. If so, do NOT login with an account which has administrator privileges, and apply strict NTFS permissions to the folder you use for file sharing and keep it well away from any personal data.
12. Do not advertise your email address.
Your email address can be searched for and use for spam very easily by programs that actively look for email addresses than can be used to spread spam. If you have your own web site DO NOT use the standard technique of using HREF and the MAILTO: method of displaying your email address, instead use Javascript to hide it from spammers and search programs (called webbots). If you visit a website and need to create a profile or login name, if it asks for an email address either enable the option to hide the address from public view or use another email address instead of your main email address.
13. Erase your hard disk before selling or recycling your old PC.
Programs and data can be easily stolen from hard drives on old PCs.A format will not clear it, you need to overwrite the data several times with a good secure erasure program which will write loads of 00000s then 11111s and 1010101s Good programs include software such as Drive Wipe, Knoppix, shred. For more permanent destruction you could use a powerful magnet, a drill or a hammer to destroy the disk (only for the most paranoid users). To recover files from a wiped disk, you can use tools such as PhotoRec and TestDisk using these steps.
17. How can I secure my Wireless Network?
Wireless networks, if unsecured can be open for anyone to use and if you have an unsecure Workgroup, people can view files on your shared folders.
To secure your wireless network, you should enable encryption of all network traffic using WPA2. You should also hide the name or SSID of your wireless network to prevent people trying to connect to it. Also, you can restrict the network to specific computers and mobile devices by putting them in a Wireless Station Access List so that unknown devices cannot connect. It is also a good idea to change the router's default admin password to prevent others from changing its settings and locking you out.
18. Can I use Multi-Factor Authentication (MFA) in Linux?
You can use two different means of logging in to Linux, besides usernames and passwords, using authentications such as Google Authenticator, Jump Cloud IaaS for Linux MFA, and MFA by ManageEngine.